Thanks to Dancho Danchev, WhoisXML API’s DNS Threat Researcher for the authentic investigations accessible here and led to the creation of this put up.
ZeuS malware traces its origin way back to 2006, when it was used to steal victims’ on-line banking credentials. In 2011, its supply code was leaked on a file-sharing web site and shortly unfold all through varied underground fora. After that, its code was enhanced by a number of cybercriminal gangs to show extra sinister behaviors like file an infection and revenue era from pay-per-click (PPC) fashions.
From 2007 until now, we nonetheless see malware like Gozi, Carberp, SpyEye, Shylock, Citadel, Tinba, Kins, Vawtrak, Emotet, Dyre, and Dridex, which have been all based mostly on ZeuS used in varied campaigns. Most of these are nonetheless Trojans or spyware and adware meant to steal victims’ personally identifiable info (PII). They are additionally accessible for buy underground.
We lately collated 17 Jabber ZeuS domains and subjected these to additional evaluation utilizing varied area and IP intelligence instruments to acquire as many artifacts as attainable. These may assist customers keep away from the dangers the menace poses.
What We Know So Far
The Jabber ZeuS gang have been recognized to make use of the following 17 domains in their campaigns:
- spyeye-trojan[.]com
- scanmyvirus[.]com
- cheapohoster[.]com
- handcrart[.]com
- algeriemonamour[.]com
- checkmyvirus[.]com
- dinerolibre[.]web
- dinerolibre[.]us
- universityofsutton[.]com
- isthisavirus[.]web
- opensc[.]biz
- isthisavirus[.]biz
- team-verification[.]com
- 2024700065[.]com
- spyeye[.]biz
- cyrto[.]com
- home-production[.]web
What We Uncovered from This Information
Subjecting the domains above to DNS lookups yielded the following 5 IP addresses:
- 74[.]208[.]236[.]172
- 151[.]106[.]96[.]114
- 162[.]255[.]119[.]20
- 80[.]76[.]218[.]240
- 95[.]128[.]49[.]240
While none of these are deemed malicious, they could be value monitoring no less than for indicators of malicious exercise attributable to their reference to the Jabber ZeuS domains.
According to reverse IP/DNS lookups, the 5 IP addresses above resolved to no less than 940 domains. And some of them are tagged “malicious” pr “suspicious” on VirusTotal. Examples embody:
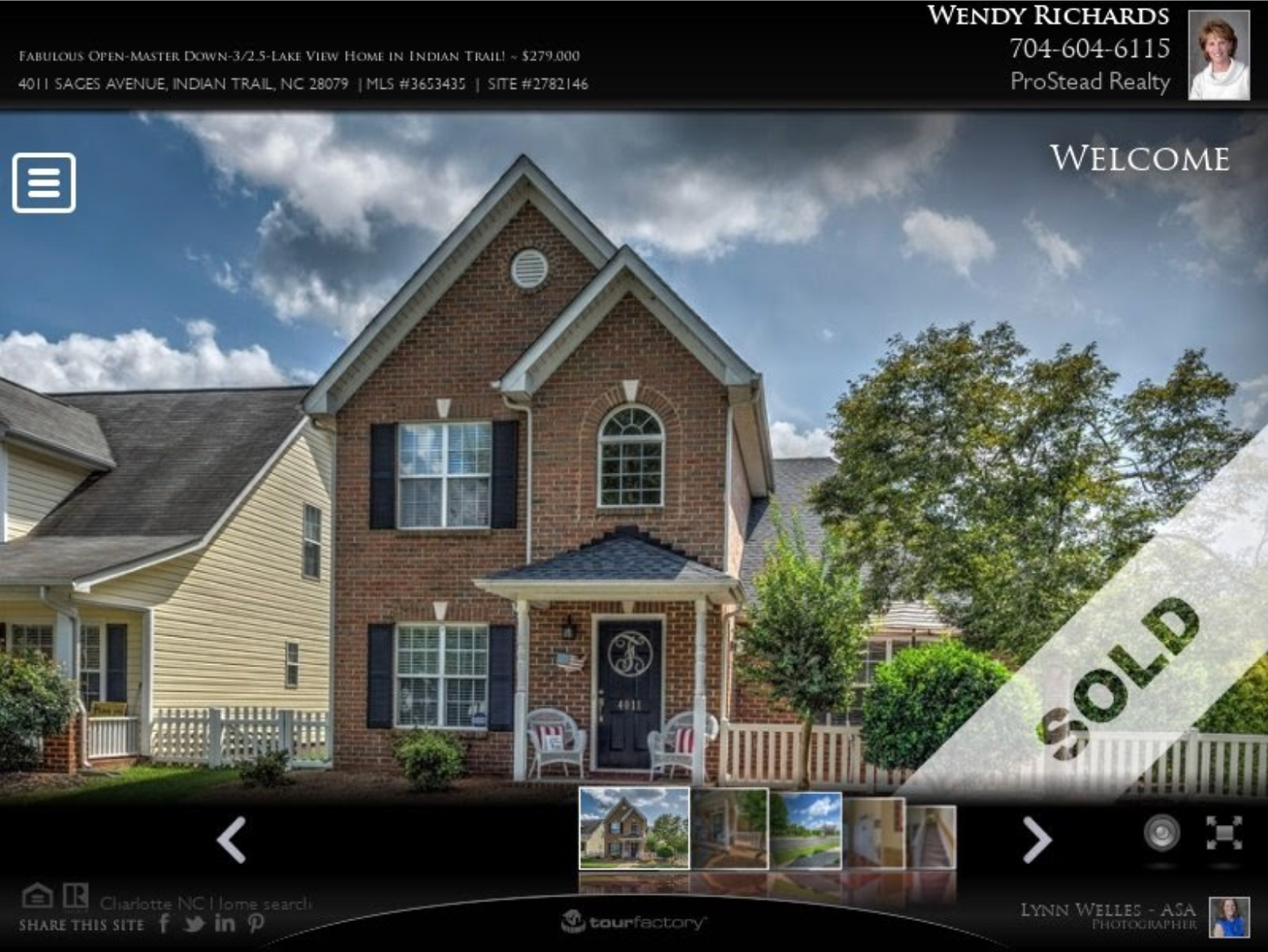
- 4011sagesave[.]information
- asdmonthly[.]com
- noticiasvendermaslibros[.]esy[.]es
- aeyana[.]com
- 34268[.]com
- alexandra-spencer[.]com
- rfh[.]icu
Screenshot lookups of the malicious domains above and the domains in our authentic record of IoCs confirmed that:
- Fourteen have been unreachable (spyeye-trojan[.]com, scanmyvirus[.]com, cheapohoster[.]com, handcrart[.]com, algeriemonamour[.]com, checkmyvirus[.]com, dinerolibre[.]web, dinerolibre[.]us, isthisavirus[.]web, opensc[.]biz, isthisavirus[.]biz, team-verification[.]com, 2024700065[.]com, and home-production[.]web).
- Three have been parked (universityofsutton[.]com, spyeye[.]biz, and asdmonthly[.]com).
- Two led to the identical area identify promoting web site (cyrto[.]com and 34268[.]com).
- One led to an actual property promoting web site (4011sagesave[.]information).

- One led to a healthcare web site (aeyana[.]com).

- One led to a consultancy service web site (alexandra-spencer[.]com).

- One led to a weblog (noticiasvendermaslibros[.]esy[.]es).

- One led to an error web page (rfh[.]icu).
From the screenshots above, we will infer that solely 9 look to be nonetheless operational. The relaxation may have been taken down already for his or her alleged ties to the Jabber ZeuS gang.
A bulk WHOIS lookup discovered data for under 5 of them (4011sagesave[.]information, rfh[.]icu, cyrto[.]com, 34268[.]com, and alexandra-spencer[.]com). All of their WHOIS data are privacy-protected so their house owners could not be recognized. But we did decide that none of the 5 of the still-active domains have been newly registered.
Historical WHOIS file lookups on them gave us three registrant organizations, one registrant identify, and three contact e mail addresses. Using these as historic reverse WHOIS search phrases supplied an inventory of 10,092 domains that could possibly be tied to the Jabber ZeuS gang. Monitoring these domains at the very least is advisable attributable to their attainable connection to the menace. Some of them could possibly be malicious or suspicious as properly.
If you want to receive an inventory of the artifacts we collated from our in-depth evaluation of the recognized Jabber ZeuS domains, please be at liberty to contact us. We are open to analysis collaboration, particularly provided that ZeuS should be alive and kicking and customers want safety from it.