Microsoft is monitoring a collection of assaults that use SEO poisoning to infect targets with a distant entry trojan (RAT) able to stealing the victims’ delicate data and backdooring their methods.
The malware delivered on this marketing campaign is SolarMarker (aka Jupyter, Polazert, and Yellow Cockatoo), a .NET RAT that runs in reminiscence and is used by attackers to drop different payloads on contaminated gadgets.
SolarMarker is designed to present its masters with a backdoor to compromised methods and steal credentials from net browsers.
The knowledge it manages to harvest from contaminated methods is exfiltrated to the command-and-control server. It may also achieve persistence by including itself to the Startup folder and modifying shortcuts on the victims’ desktop.
In April, eSentire researchers observed menace actors behind SolarMaker flooding search outcomes with over 100,000 net pages claiming to present free workplace kinds (e.g., invoices, questionnaires, receipts, and resumes).
However, they might as a substitute act as traps for enterprise professionals looking for doc templates and infect them with the SolarMaker RAT utilizing drive-by downloads and search redirection by way of Shopify and Google Sites.
Switches to abuse AWS and Strikingly
In more moderen assaults noticed by Microsoft, the attackers have switched to keyword-stuffed paperwork hosted on AWS and Strikingly, and at the moment are concentrating on different sectors, together with finance and schooling.
“They use 1000’s of PDF paperwork stuffed w/ SEO key phrases and hyperlinks that begin a series of redirections ultimately main to the malware,” Microsoft stated.
“The assault works through the use of PDF paperwork designed to rank on search outcomes. To obtain this, attackers padded these paperwork with >10 pages of key phrases on a variety of matters, from ‘insurance coverage type’ and ‘acceptance of contract’ to ‘how to take part SQL’ and ‘math solutions’.”
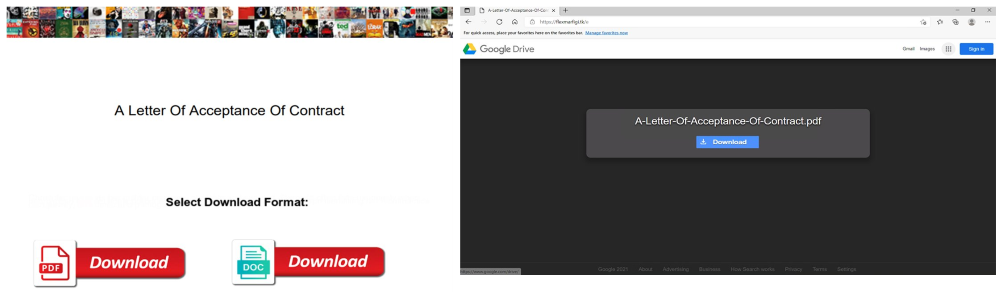
Once the victims discover one of many maliciously crafted PDFs and open them, they’re prompted to obtain one other PDF or DOC doc containing the knowledge they’re searching for.
Instead of gaining entry to the information, they’re redirected by a number of web sites utilizing .website, .tk, and .ga TLDs to a cloned Google Drive net web page the place they’re served the final payload, the SolarMaker malware.
The SolarMaker developers are believed to be Russian-speaking threat actors based mostly on Russian to English translation misspelling, in accordance to Morphisec.
The Morphisec researchers additionally discovered that most of the malware’s C2 servers are positioned in Russia, though many had been now not energetic.
“The TRU has not but noticed actions-on-objectives following a SolarMarker an infection, however suspect any variety of potentialities, together with ransomware, credential theft, fraud, or as a foothold into the sufferer networks for espionage or exfiltration operations,” eSentire’s Threat Response Unit (TRU) added.